Step into the world of security testing and be aware of concerns and recommendations that you can consider when doing security testing. When working on a project, you will interact with internal or external security teams that scan your applications and present the findings. What if you could identify the security issues earlier and fix them before reaching the security team? How can you do this? A way is by using OWASP ZAP security scan tool.

Introduction to Zap Security tool
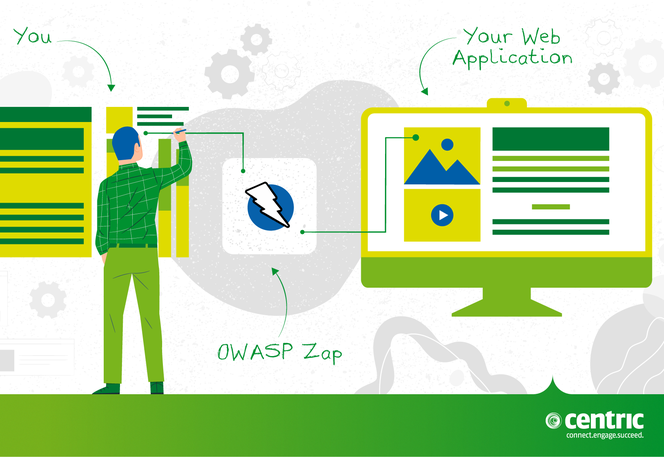
Penetration testing helps you find vulnerabilities in a system/application before an attacker.
OWASP Zap is a tool used to perform penetration tests. The main purpose of this tool is oriented toward web applications.
ZAP creates a proxy server and makes the traffic from a website pass through that server. You can say that it is positioned between the browser and the web application so that it can intercept and inspect the messages sent between those two, modify the content if it is necessary and then send the requests to the destination.
Maintained by OWASP, ZAP has a large community of people who create new features and add-ons that have made this tool very versatile. What is nice is the fact that ZAP is available for any operating system and also Docker. You can use it both in the graphical interface version, but also from the command line.
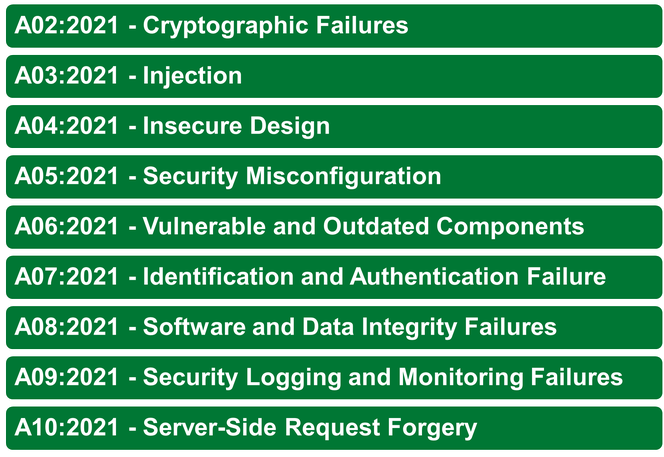
When thinking about security, it is important to know about the OWASP Top 10, which is also a reference to Zap. Below you can find the list of Web Application Security Risks (2021).
Find more about this here.
If you want to work with Zap, you need to install it on your local machine, below you can find out some tips and tricks for installation:
- Java is required as a prerequisite, at least version 7.
- After the installation, you will need to configure the proxy by going to Tools menu > Select Options > Select Local Proxy
- The browser you will run your application should also have the same proxy configured.
After the installation, you will need to configure some settings. ZAP works with SSL certificates which can be generated from Tools > Options > Dynamic SSL Certificates using the Save button. This generated Root CA certificate should be imported into the browser as a trusted one; without it you will not be able to intercept the requests and scan your application.
Note: The certificate should not be shared with third parties.
Zap has four modes of security testing, which have different scopes. Make sure that you are aware of what each of them does before starting a scan:
- Safe Mode - no potentially dangerous attack will be generated
- Protected Mode - perform (potentially) dangerous attacks on defined URLs under a controlled context
- Standard Mode – no restrictions; any attack can be made
- ATTACK Mode – perform an attack on discovered nodes
After choosing the security testing mode, you will need to decide on the next step which kind of attack you want to perform by using one of the following types of security attacks:
Passive scan
- Spider scan - automatically discovers new URL resources to visit starting from a list of URLs by looking in HTML for elements like href, link, frame. Find more about this here.
- Ajax spider scan – discovers hyperlinks to visit by looking in JavaScript code
Active scan
- It will perform penetration tests on the web application. Consider the legal aspects.
ZAP has a general policy called Default which can be found in Analyse > Scan Policy Manager that applies to any type of scan. This policy can be modified with your desired settings:
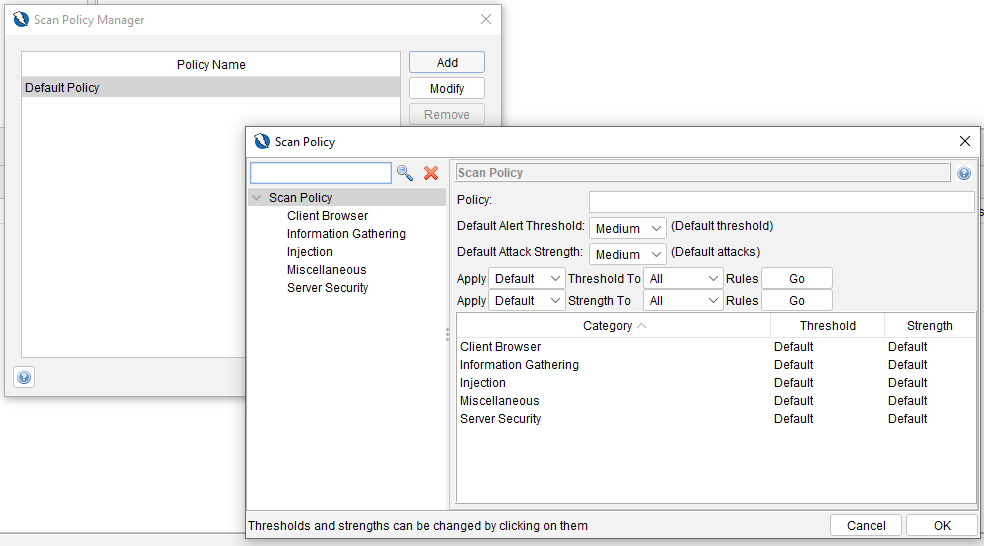
You can set multiple policies and use one at a time, depending on your security test scope.
Particularly for active scan, we can set an extra policy related to the number of concurrent hosts and threads, time for one specific security rule to be checked, or how long the run should take (if you change these two last options, you should consider that it is possible not to discover all the issues). Delay when scanning refers to leaving a time between requests, but here we must consider that we will force ZAP to wait a specific time interval between requests, which means that it is possible to increase the execution time. Also, for Active Scan, ZAP offers another very useful option called “Active scan input Vectors” – here, we can see the attack types that ZAP will execute when running an active scan, and we can select and deselect the ones that are in our focus or not.
For the running part, you can choose between Manual Scan or Automated Scan:
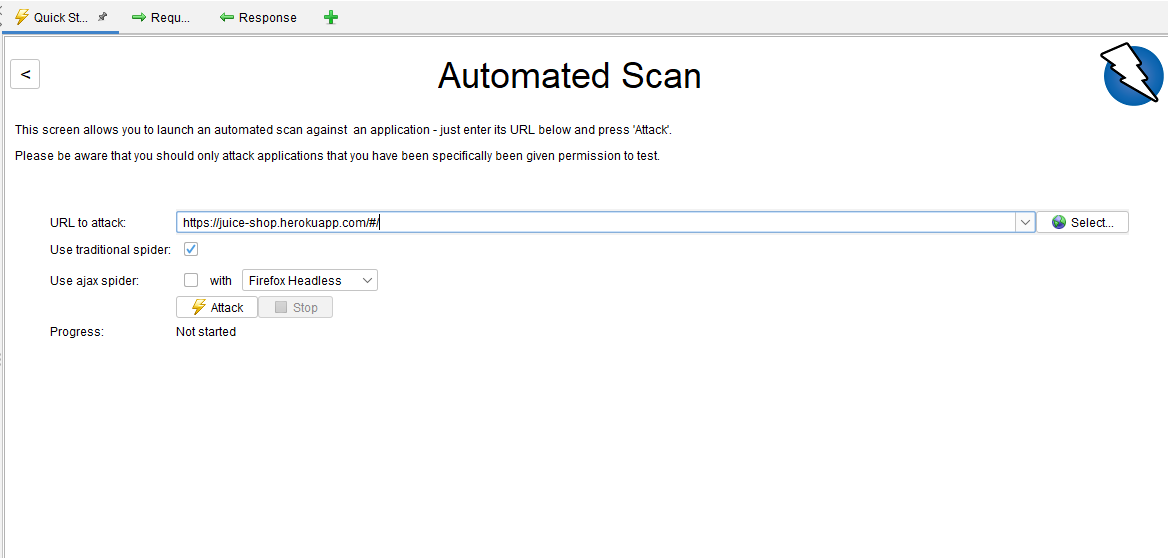
After performing a scan, you can check the results of the scan using the reporting features by going to Report > Generate Report.
Zap allows downloading reports with the vulnerabilities discovered after a run, structured by security level, the number of times the vulnerability was found, and a solution to solve it. The report can be extracted in different formats such as HTML, XML, Markdown, or JSON.
You will encounter terms like Authentication, Session, and User Management.
More about these you can find here.
ZAP integration
You can run ZAP with different Continuous Integration Servers, such as Jenkins, Azure DevOps, or others. You can also run it from the command line using PowerShell or from Docker Container.
I worked with Jenkins, and it is quite simple to customize everything related to the chosen type of scan. Jenkins plugin enables several ZAP operations within the pipeline such as Spider Scans, AJAX Spidering, Active Scan, Managing Sessions, Defining Context, and correlate results.
With Azure DevOps, from everything I have managed to find out so far, a viable solution would be to use Docker and I have left at the end some links with some examples and the OWASP documentation for Docker integration with ZAP.
If you want to run ZAP from the command line and create some PowerShell scripts that could then be integrated into Azure DevOps, it is a more challenging task. For now, ZAP has only a few commands that can be used without a User Interface (UI): you can only create a quick scan and you will not have data for users, context, exclude from context, etc.
Security Concerns and Recommendations
- Have in mind asking permission to do this kind of scan (think about the legal aspects)
- Be aware that the system will be affected by these scans
- Announce planned security tests
- Identify the scan level for your application
- Keep the reports private and label them as Confidential
- Ensure that ports are configured properly
- Verify and validate the findings from the scans (be aware of False positives)
- Ensure the scan goes through the essential functionalities from your application
Security playground:
- Site examples:
- Juice Shop: https://juice-shop.herokuapp.com/#/
- OWASP’s online vulnerable applications: https://owasp.org/www-project-vulnerable-web-applications-directory/
- Offline resources:
- DVWA: https://dvwa.co.uk/
- OWASP Mutillidae: https://github.com/webpwnized/mutillidae
- bWAPP: http://www.itsecgames.com/
References and useful links:
- https://www.zaproxy.org/docs/desktop/ui/dialogs/options/dynsslcert/#install
- https://www.zaproxy.org/faq/is-there-any-danger-when-scanning-with-zap-against-a-live-website-e-g-create-delete-update-corrupt-data/
- https://we45.com/blog/7-features-that-make-zap-great-for-application-security-testing/
- https://resources.infosecinstitute.com/topic/introduction-owasp-zap-web-application-security-assessments/
- https://www.zaproxy.org/docs/desktop/cmdline/
- https://www.zaproxy.org/docs/docker/
- https://devblogs.microsoft.com/premier-developer/azure-devops-pipelines-leveraging-owasp-zap-in-the-release-pipeline/

